Cybersecurity best practices are more important than ever in today's digital landscape, where threats lurk around every corner. From securing your passwords to training employees and implementing network security measures, this guide will walk you through essential steps to protect your organization from potential cyber threats.
As we delve deeper into each aspect of cybersecurity best practices, you'll gain valuable insights on how to fortify your defenses and safeguard your sensitive information from malicious actors.
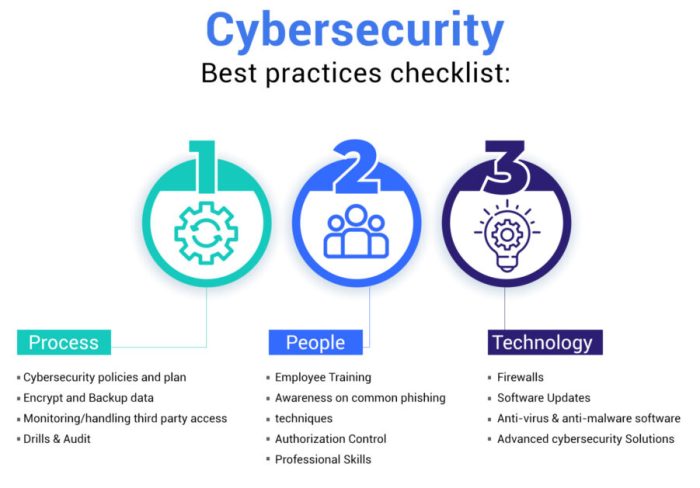
Importance of Cybersecurity Best Practices
In today's digital landscape, cybersecurity best practices are more crucial than ever before. With the increasing frequency and sophistication of cyber threats, organizations and individuals must prioritize implementing robust security measures to protect sensitive data and prevent potential cyber attacks.Recent cyber threats, such as ransomware attacks on major organizations, data breaches exposing millions of personal records, and sophisticated phishing scams targeting unsuspecting individuals, highlight the significance of adhering to cybersecurity best practices.
These incidents not only result in financial losses but also damage reputation and trust among customers and stakeholders.Neglecting cybersecurity best practices can have severe consequences, including unauthorized access to confidential information, financial fraud, identity theft, and even system downtime. The costs associated with recovering from a cyber attack can be substantial, impacting both the bottom line and the overall operations of a business or individual.
Therefore, it is essential to proactively implement and maintain effective cybersecurity measures to mitigate risks and safeguard against potential threats.
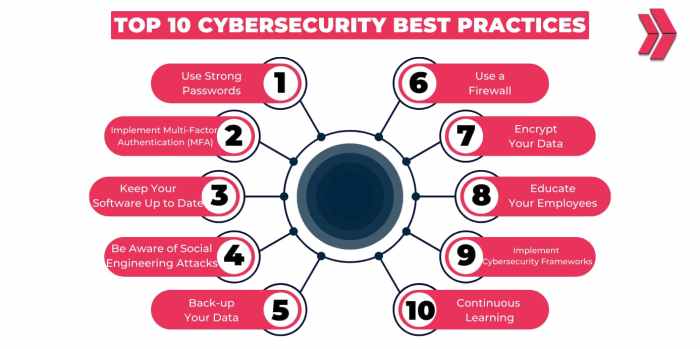
Implementing Strong Password Policies
Creating secure passwords and using multi-factor authentication are crucial steps in enhancing cybersecurity. Additionally, password management tools can further strengthen security measures.
Guidelines for Creating Secure Passwords
- Use a combination of uppercase and lowercase letters, numbers, and special characters.
- Avoid using easily guessable information like birthdays, names, or common phrases.
- Ensure passwords are at least 12-16 characters long for increased complexity.
- Regularly update passwords and avoid reusing them across multiple accounts.
Importance of Multi-Factor Authentication
Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of identification before accessing an account. This can include a password, fingerprint scan, or security token.
Password Management Tools
- LastPass:A popular password manager that securely stores and organizes passwords.
- 1Password:Provides a secure vault for storing passwords, credit card information, and other sensitive data.
- Bitwarden:An open-source password manager with end-to-end encryption for enhanced security.
Regular Software Updates and Patch Management
Keeping software up to date is crucial in maintaining a secure and resilient cybersecurity posture. Regular software updates and patch management play a vital role in protecting systems and data from potential cyber threats and vulnerabilities.
Importance of Keeping Software Up to Date
Software updates often include patches that address security vulnerabilities discovered by developers or reported by users. By installing these updates promptly, organizations can strengthen their defenses against cyber attacks and reduce the risk of unauthorized access to sensitive information.
Risks of Running Outdated Software
Running outdated software exposes systems to various risks, including malware infections, data breaches, and system crashes. Hackers often exploit known vulnerabilities in outdated software to gain unauthorized access to networks and compromise sensitive data. Therefore, failing to update software regularly can leave organizations vulnerable to cyber threats.
Role of Patch Management in Cybersecurity
Patch management involves the process of identifying, acquiring, testing, and applying patches to software systems to eliminate security vulnerabilities. By implementing an effective patch management strategy, organizations can ensure that their systems are up to date with the latest security patches, reducing the likelihood of exploitation by cybercriminals.
Employee Training and Awareness
Employee training and awareness play a crucial role in maintaining cybersecurity within an organization. Educating employees on cybersecurity best practices can help prevent data breaches, phishing attacks, and other cyber threats.
Common Social Engineering Tactics
- Phishing emails: Cybercriminals send emails pretending to be from a legitimate source to trick employees into revealing sensitive information or clicking on malicious links.
- Pretexting: Scammers create a fake scenario to manipulate employees into providing confidential information or access to systems.
- Tailgating: Intruders gain unauthorized access to secure areas by following an employee with legitimate access.
Tips for Creating an Effective Cybersecurity Training Program
- Provide regular training sessions: Conduct ongoing training to ensure employees are up to date on the latest cybersecurity threats and best practices.
- Simulate phishing attacks: Test employees' awareness with simulated phishing emails to help them recognize and report suspicious messages.
- Encourage reporting: Create a culture where employees feel comfortable reporting any cybersecurity incidents or concerns promptly.
- Offer incentives: Reward employees who demonstrate a strong commitment to cybersecurity practices and awareness.
Network Security Measures
Securing networks is crucial in preventing unauthorized access to sensitive information and protecting against cyber threats. Implementing network security measures helps in safeguarding data integrity, confidentiality, and availability.
Role of Firewalls, Intrusion Detection Systems, and Encryption
- Firewalls act as a barrier between internal networks and external threats, filtering incoming and outgoing network traffic based on set security rules.
- Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity or potential security breaches, alerting administrators to take necessary actions.
- Encryption ensures that data transmitted over networks is encoded in a secure manner, making it unreadable to unauthorized users.
Best Practices for Securing Wireless Networks
- Change default SSID and password: Replace default network names and passwords with unique and complex ones to prevent unauthorized access.
- Enable network encryption: Use WPA3 or WPA2 encryption protocols to secure wireless communications and protect data from interception.
- Implement MAC address filtering: Only allow specific devices with approved MAC addresses to connect to the wireless network, enhancing security.
- Disable SSID broadcast: Hide the network name from being broadcasted publicly to reduce the visibility of the wireless network to potential attackers.
Incident Response and Disaster Recovery Planning
When it comes to cybersecurity, having an incident response plan and disaster recovery plan in place is crucial to minimize the impact of any potential security breaches or disasters. These plans Artikel the steps to be taken in case of a cyber incident or a catastrophic event, ensuring that the organization can respond effectively and recover quickly.
Importance of an Incident Response Plan
An incident response plan is essential for organizations to detect, respond to, and recover from cybersecurity incidents in a timely and organized manner. Key components of an effective incident response plan include:
- Clearly defined roles and responsibilities for incident response team members.
- Identification of potential security threats and vulnerabilities.
- Establishment of communication protocols for reporting and escalating incidents.
- Documentation of incident response procedures and processes.
Regular Testing and Updating of Disaster Recovery Plans
Regular testing and updating of disaster recovery plans are equally important to ensure that the organization can recover critical systems and data in the event of a disaster. This involves:
- Conducting regular tabletop exercises and simulations to test the effectiveness of the plan.
- Reviewing and updating the plan based on lessons learned from testing and real incidents.
- Ensuring that the plan aligns with the evolving threat landscape and technological advancements.
- Training employees on their roles and responsibilities in implementing the disaster recovery plan.
Final Review
In conclusion, by following these cybersecurity best practices diligently, you can significantly reduce the risk of cyber attacks and ensure the safety of your digital assets. Stay informed, stay vigilant, and stay secure in this ever-evolving digital world.
Q&A
How often should I update my passwords?
It is recommended to change your passwords every 3-6 months to maintain security.
What is the role of encryption in network security?
Encryption helps protect data in transit and at rest by encoding it so that only authorized parties can access it.
Why is employee training crucial for cybersecurity?
Educating employees helps create a security-conscious culture and reduces the risk of falling victim to social engineering attacks.